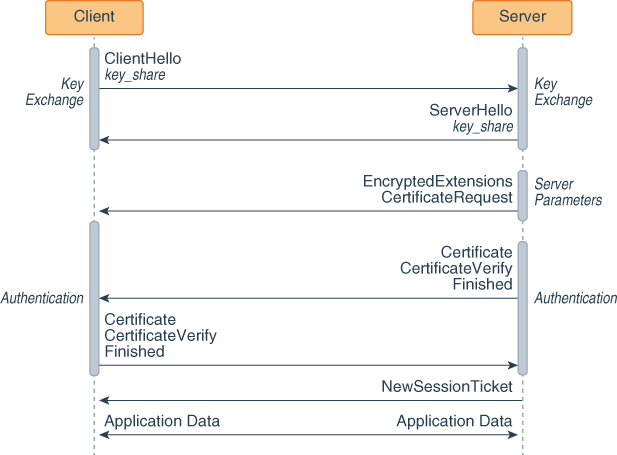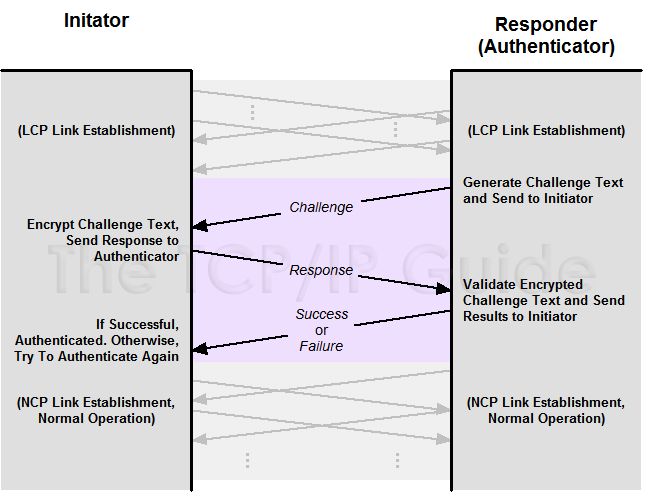
The TCP/IP Guide - PPP Authentication Protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP)

What is Challenge-Handshake Authentication Protocol (CHAP) and how does it work? - The Security Buddy
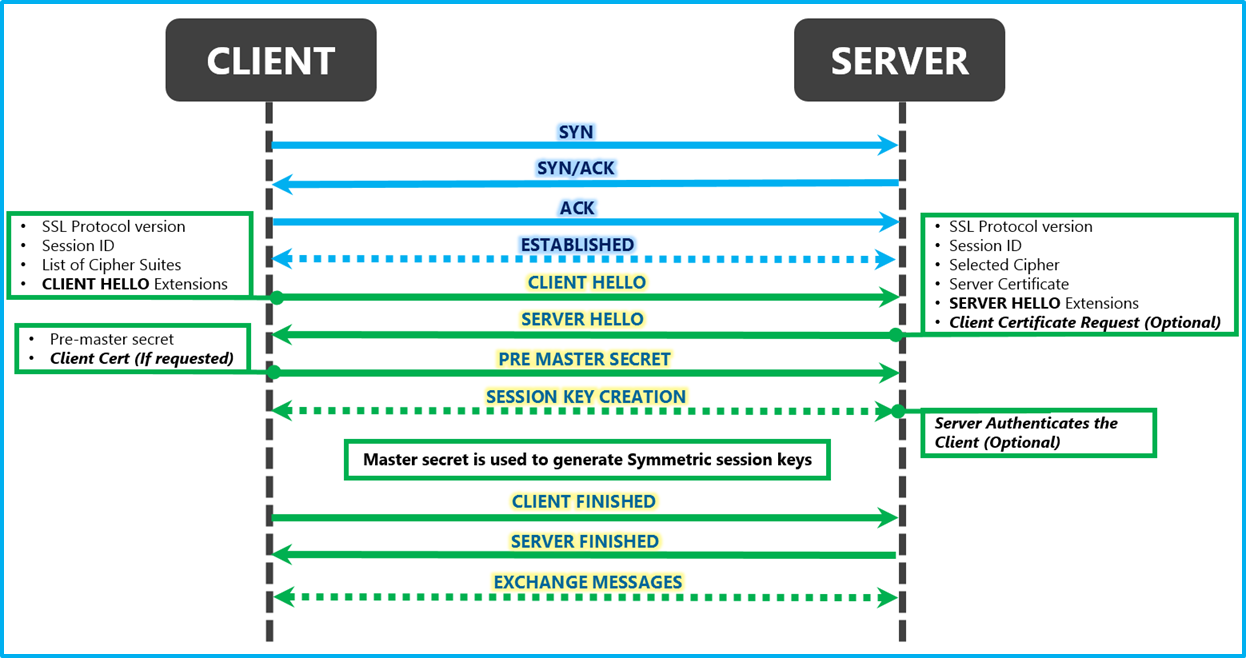
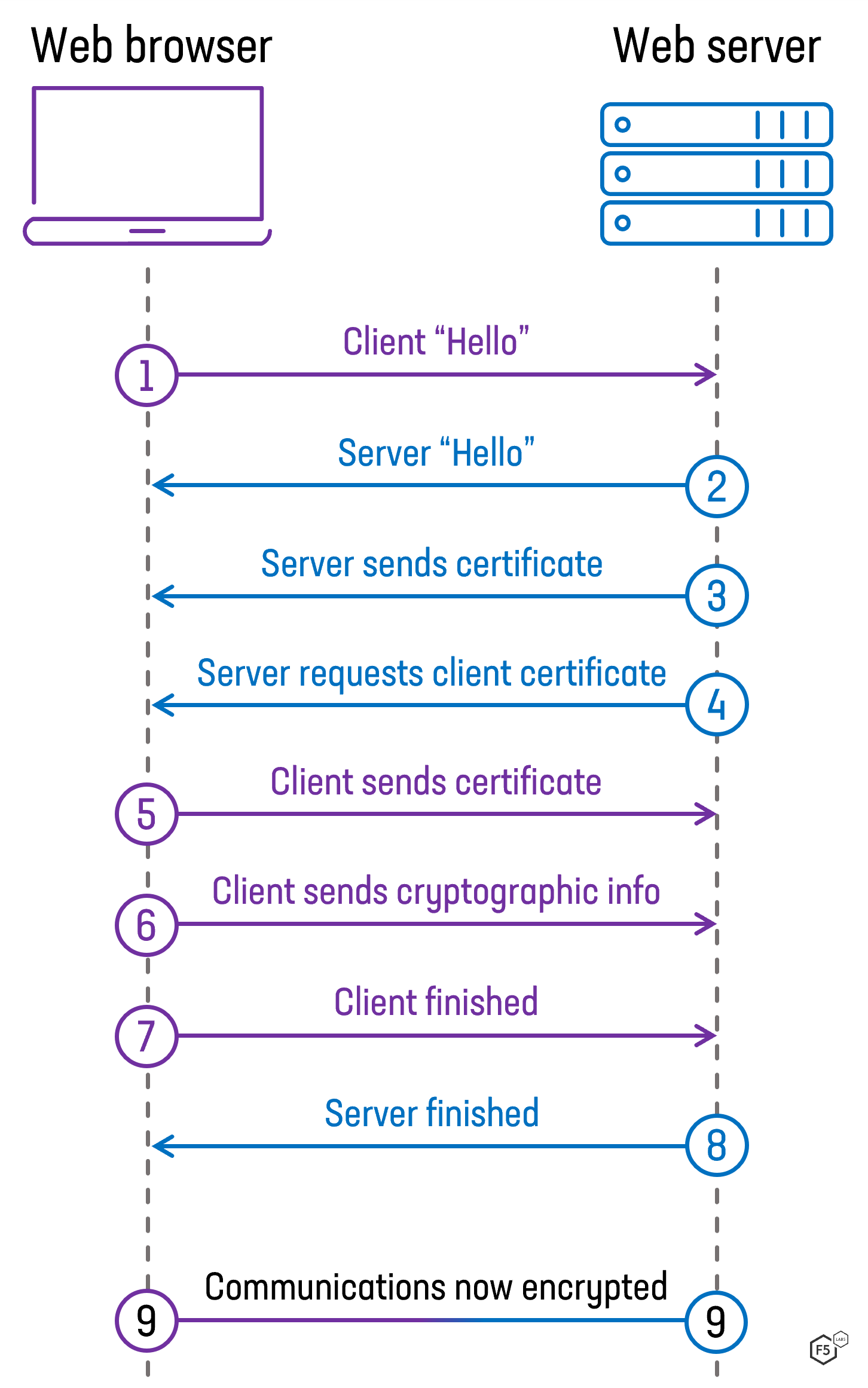
An overview of the SSL Handshake. In this post I will give an overview of… | by Robert van Rijn | Medium

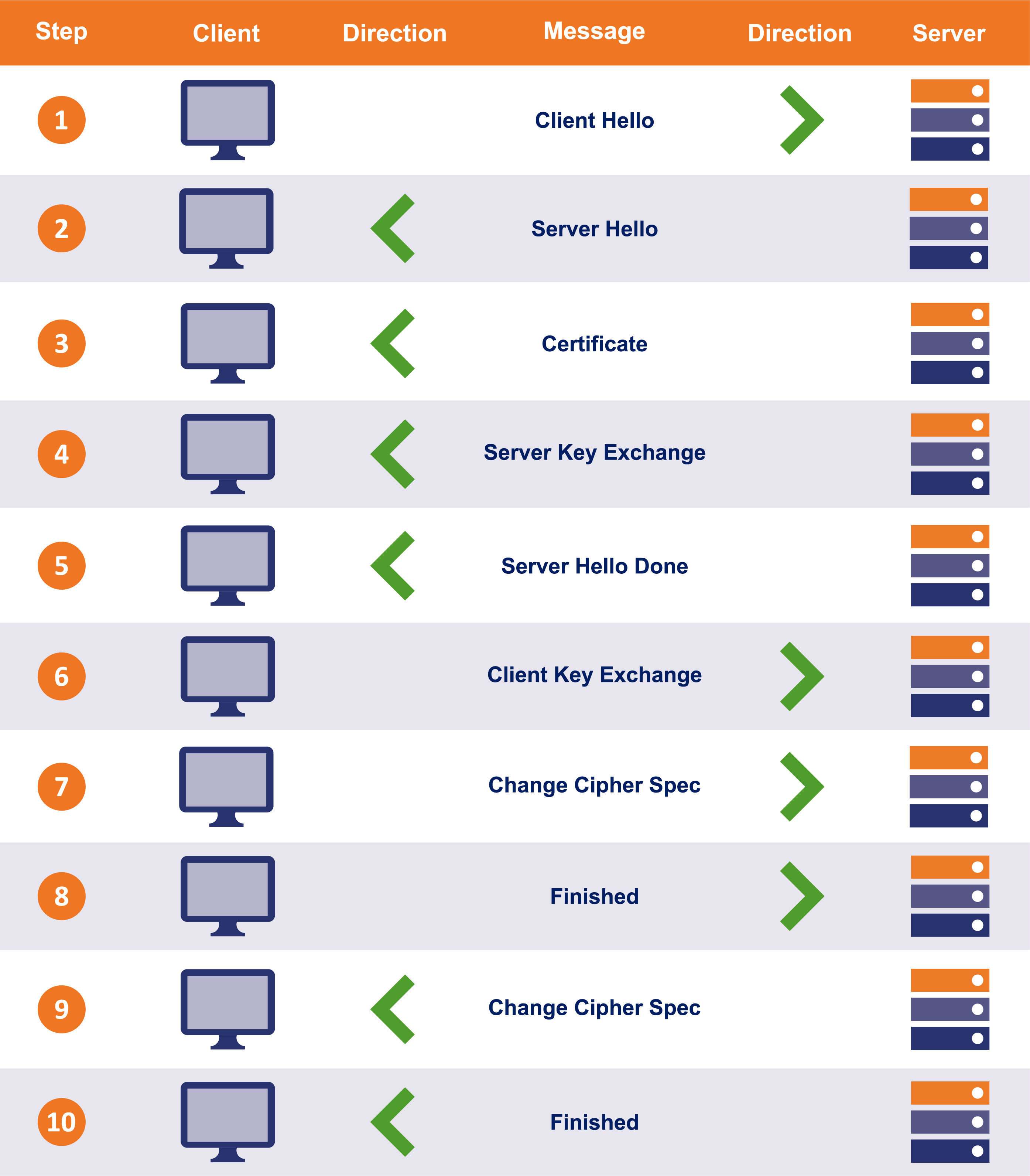
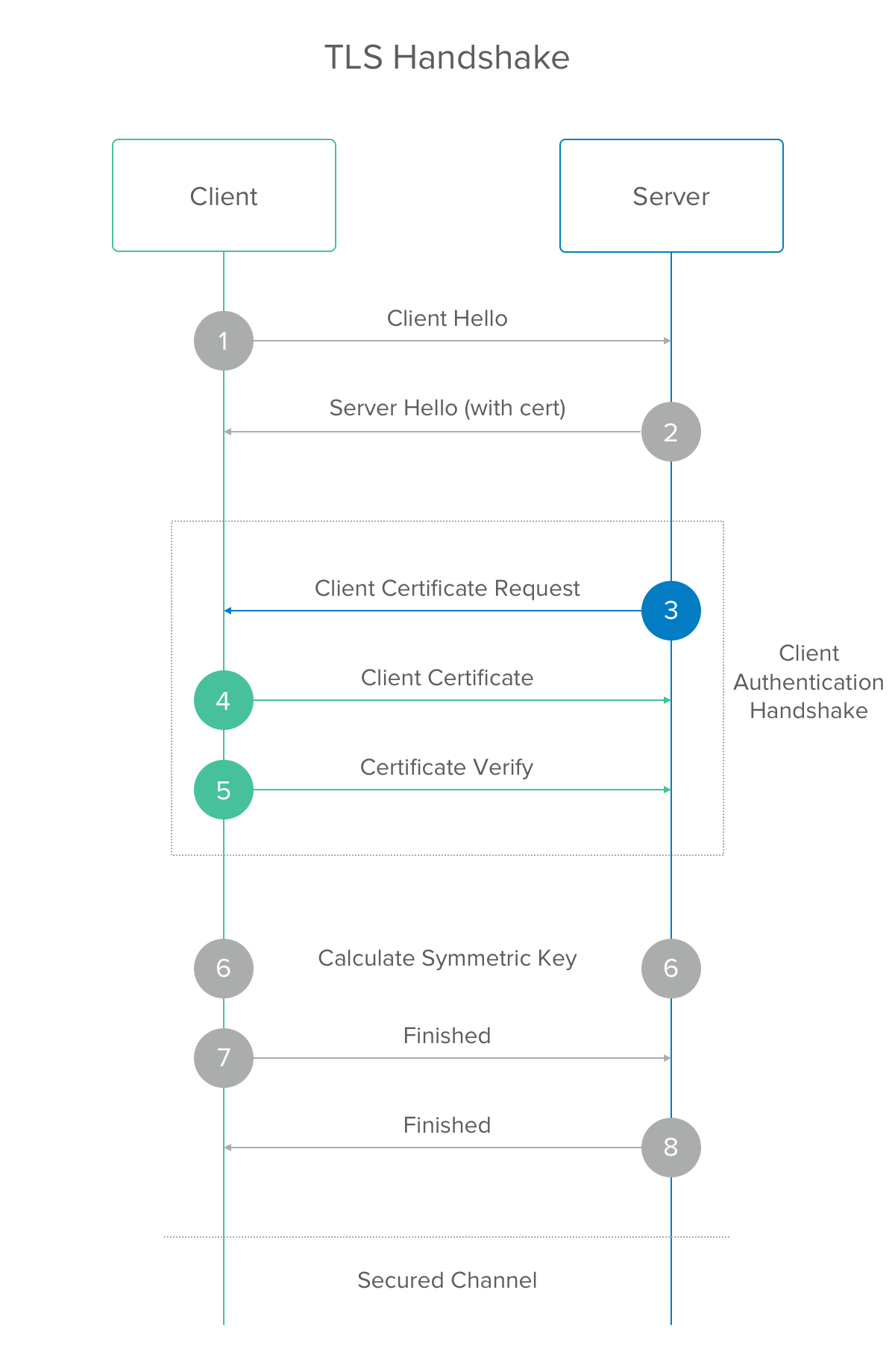
TCP and TLS handshake: What happens from typing in a URL to displaying a website? (Part 2) | by Alysa Chan | Medium

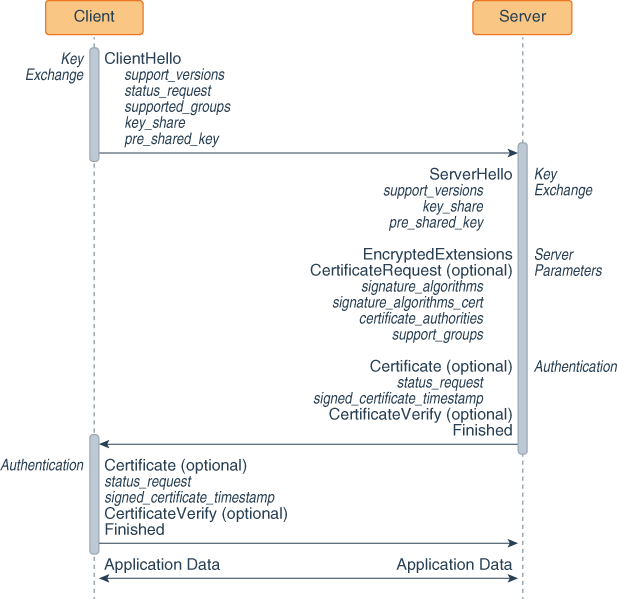
On post-handshake authentication and external PSKs in TLS 1.3 | Journal of Computer Virology and Hacking Techniques
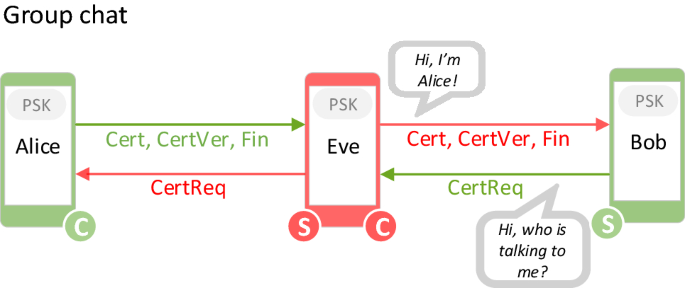
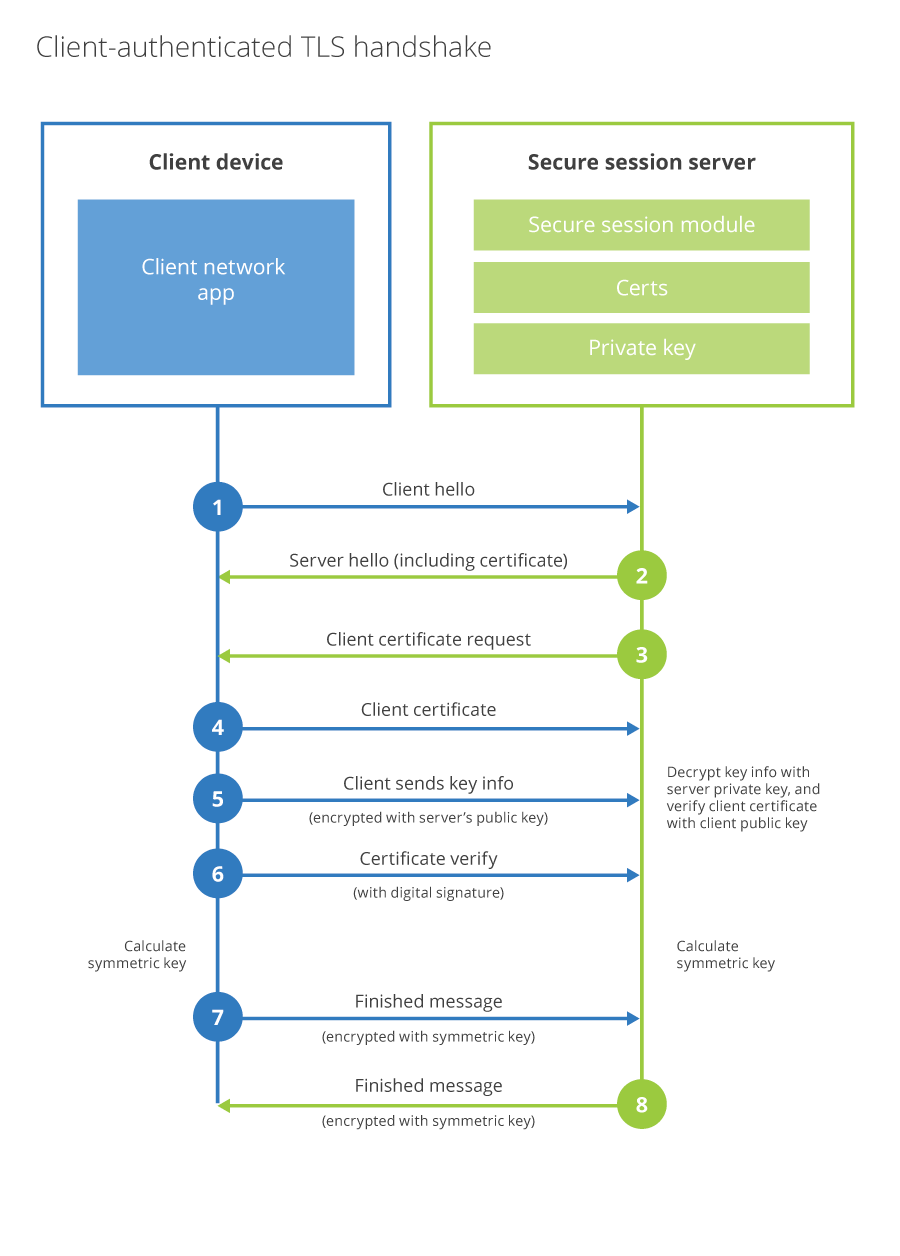

![PDF] Continuing to reflect on TLS 1.3 with external PSK | Semantic Scholar PDF] Continuing to reflect on TLS 1.3 with external PSK | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fbc666dcb763e7c9e4ccae1fb543475e76126bf/5-Figure1-1.png)