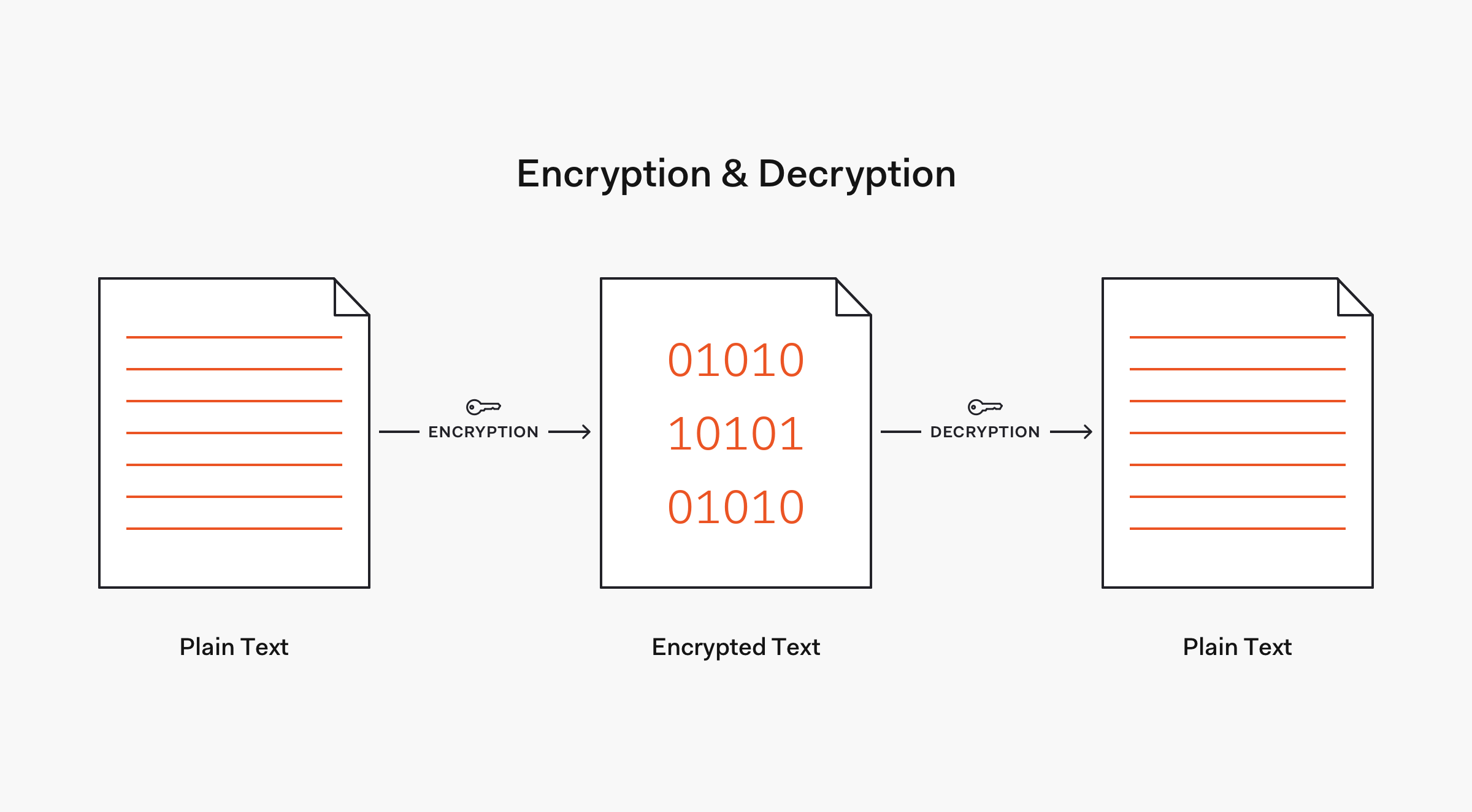
GitHub - zynesis/secure-password-transport: Quick script to demonstrate how PKI can enable secure password transmission
![PDF] Secure Password Transmission for Web Applications over Internet using Cryptography and Image Steganography | Semantic Scholar PDF] Secure Password Transmission for Web Applications over Internet using Cryptography and Image Steganography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5e6fa9a49557a7f6de2d1863c12a7e7f6113f130/7-Figure3-1.png)
PDF] Secure Password Transmission for Web Applications over Internet using Cryptography and Image Steganography | Semantic Scholar