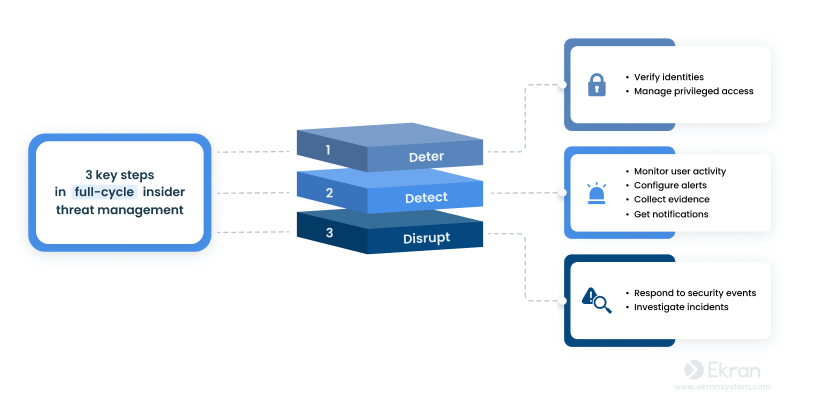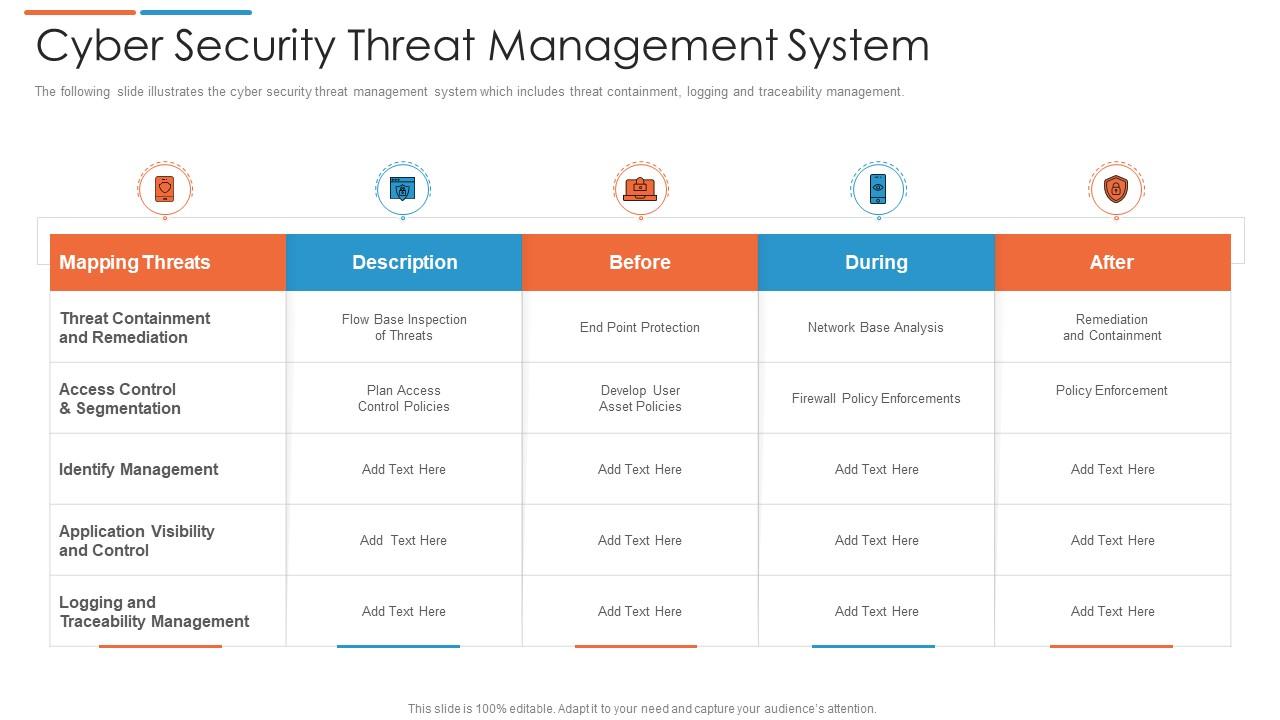
Cyber Security Threat Management System | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

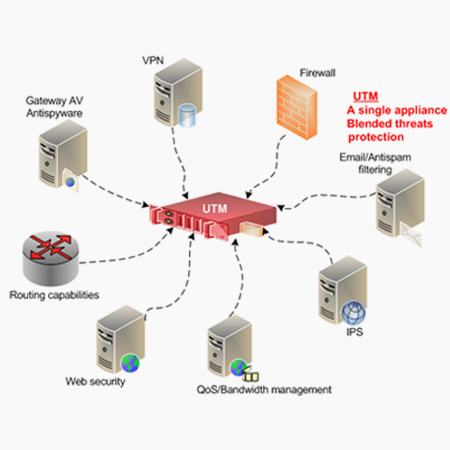
Yukta Agarwal on LinkedIn: #unifiedthreatmanagement #security #cybersecurity #integratedthreatdefense…

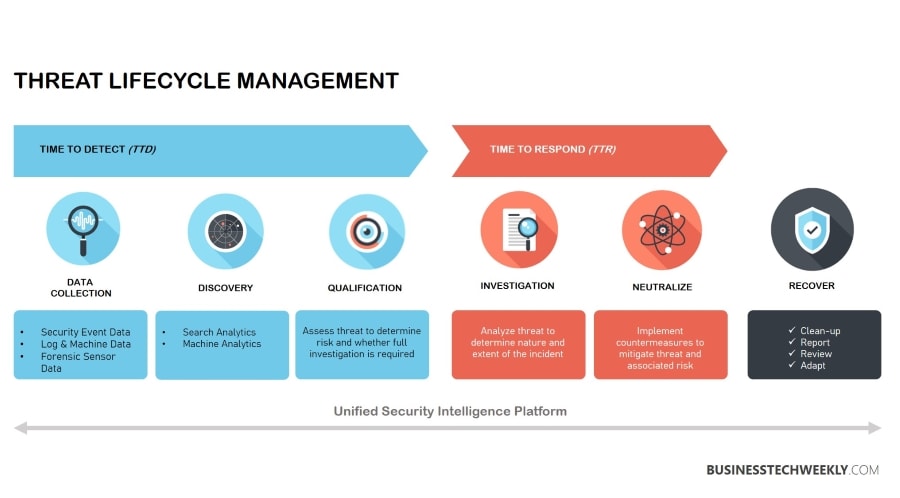
Cyber Threat Monitoring Systems - Comparing Attack Detection Performance of Ensemble Algorithms | SpringerLink

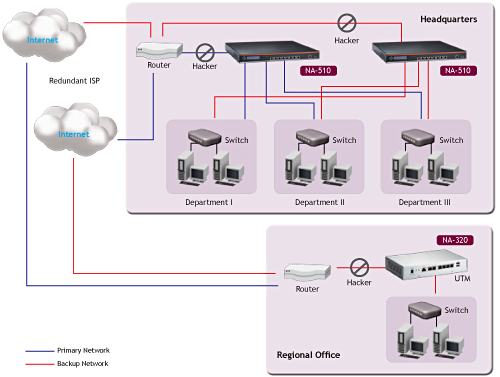
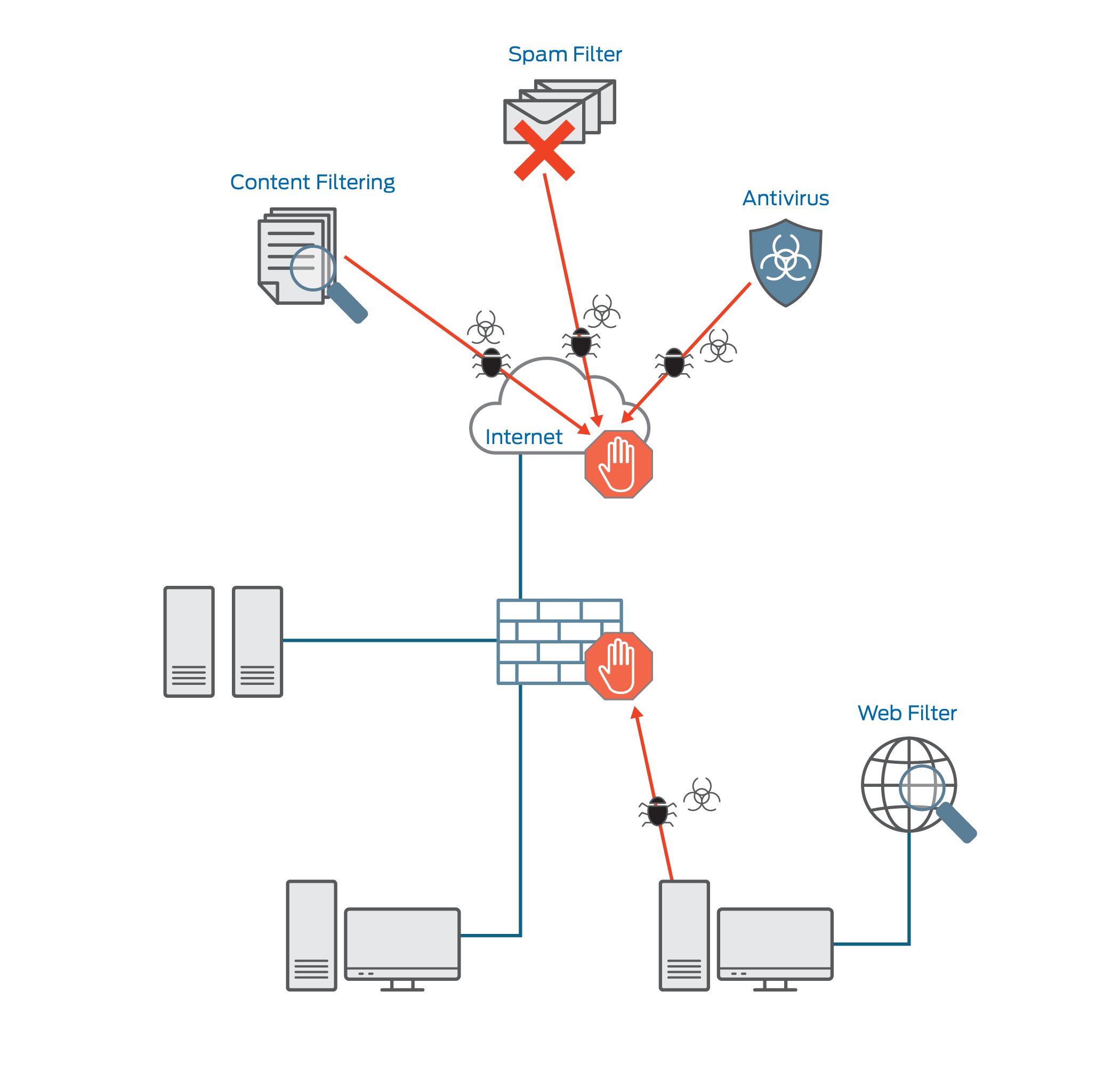
Figure 4 from Unified Threat Management System Approach for Securing SME's Network Infrastructure | Semantic Scholar